About Lesson
Digital Signatures: Integrity in public-key systems :
Digital signatures provide integrity in public-key systems by ensuring that a message has not been altered or tampered with during transmission. Here’s how it works:
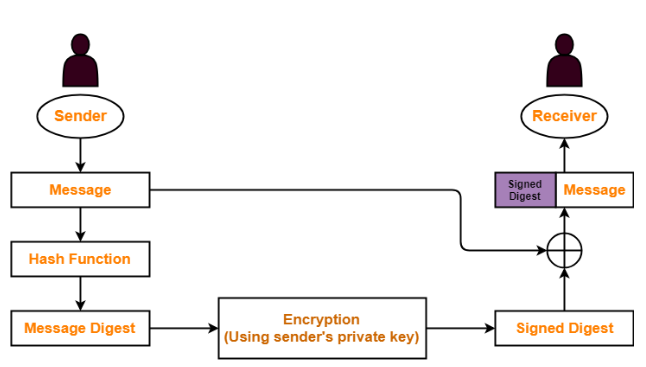
- Message Digest: Before signing a message, the sender calculates a unique fixed-size string of characters called a message digest or hash value from the original message using a cryptographic hash function. This digest acts as a unique fingerprint of the message.
- Signing the Digest: The sender then encrypts the message digest using their private key, creating a digital signature. This signature is appended to the message or sent alongside it.
- Verification: Upon receiving the message and signature, the recipient decrypts the signature using the sender’s public key, revealing the original message digest.
- Digest Comparison: The recipient independently calculates the message digest of the received message using the same cryptographic hash function used by the sender.
- Comparison: If the calculated digest matches the one decrypted from the signature, it indicates that the message has not been altered during transmission. This ensures integrity, as any changes to the message would result in a different digest, making the signature invalid.
In summary, digital signatures in public-key systems provide integrity by allowing recipients to verify that a message has not been modified or corrupted during transmission, ensuring that the information received is authentic and trustworthy.
Uses Of Digital Signatures:
Uses of Digital Signatures:
- Document Integrity: Just like signing a paper document, digital signatures ensure that electronic documents, like contracts or agreements, have not been altered or tampered with since they were signed.
- Authentication: Digital signatures verify the identity of the sender. They assure recipients that the message or document is indeed from the claimed sender and not from an impostor.
- Non-repudiation: Once a message is digitally signed, the sender cannot deny sending it. Recipients can prove the sender’s involvement, providing legal protection in disputes.
- Secure Transactions: Digital signatures are crucial in secure online transactions, like e-commerce or banking, ensuring that both parties agree to the transaction terms and that payment details are secure.
- Software Distribution: Digital signatures are used to verify the authenticity and integrity of software updates or downloads. Users can trust that the software has not been tampered with or altered by unauthorized parties.
- Legal Documents: In legal proceedings, digital signatures hold the same legal weight as handwritten signatures. They’re used for signing contracts, agreements, or any legally binding documents.
