Public key Cryptography:
Public key cryptography is like having a magical lock that everyone can use, but only you have the key to open it. In this system, there are two keys: a public key and a private key. You share the public key openly, like displaying the lock, so anyone can use it to encrypt messages. However, only you possess the private key, which is like the secret key to unlock those messages. This way, even though everyone can send you encrypted messages using the public key, only you can decrypt and read them with your private key.
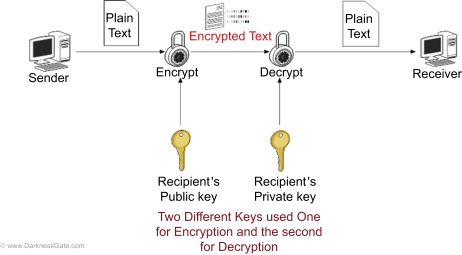
secure conversation using public-key cryptography:
In a basic secure conversation using public-key cryptography, the sender encrypts the message using the receiver’s public key. Remember that this key is known to everyone. The encrypted message send tot he receiving end, where the receiver will decrypt the message with his private key. only reciever can decrypt the message with his private key because no one else has the private key.
Pros And Cons of Public-key Systems:
Pros:
- Security: Public-key systems offer strong security because they use asymmetric encryption, making it extremely difficult for unauthorized parties to decrypt messages without the private key.
- Key Distribution: Public keys can be freely distributed and shared without compromising security. This simplifies the process of exchanging encryption keys compared to symmetric key systems, where keys must be securely exchanged beforehand.
- Digital Signatures: Public-key systems facilitate digital signatures, allowing individuals to sign documents or messages with their private key. Recipients can verify the signature using the sender’s public key, ensuring the authenticity and integrity of the message.
- Non-repudiation: Due to the use of digital signatures, public-key systems provide non-repudiation, meaning the sender cannot deny sending a message or signing a document, as their identity can be verified with their private key.
- Scalability: Public-key systems are highly scalable since each user only needs to generate and manage their own key pair, regardless of the number of communication partners.
Cons:
- Computational Overhead: Public-key cryptography typically requires more computational resources compared to symmetric-key cryptography, making it slower and more resource-intensive, especially for large volumes of data.
- Key Management: While public keys can be freely distributed, managing private keys securely is crucial. If a private key is compromised, it can lead to unauthorized access to encrypted data or impersonation of the key owner.
- Key Exchange Problem: Despite the convenience of freely distributing public keys, securely exchanging public keys remains a challenge. Man-in-the-middle attacks can occur if an attacker intercepts and replaces public keys during transmission.
- Complexity: Public-key systems are conceptually more complex than symmetric-key systems, requiring a deeper understanding of cryptographic principles and key management practices.
- Potential Vulnerabilities: While public-key systems are generally secure, they are not immune to attacks. Vulnerabilities in encryption algorithms or implementation flaws can potentially compromise the security of the system.
