Cryptography is the practice of securing communication and data by converting plain text into unintelligible code, called ciphertext, using algorithms and keys. This ensures that even if unauthorized individuals intercept the message, they cannot understand its contents without the corresponding decryption key.
Key-based Algorithm:
A key-based algorithm uses an encryption key to encrypt the message . this means that the encrypted message is generated using not only the meassage , but also using the ‘key’:
The receiver can then use a decryption key to decrypt the message. this means that the decryption algorithm doesn’t rely on the encrypted message. it also needs a ‘key’
some algorithm use the same key to encrypt and decrypt, and some do not . let’s take a simple example , we might be intrested in transmitting the following message.
1 2 3 4 5 6 5 4 3 2 1
we will now choose a key to encrypt a message. let us suppose the key is “3242” to encrypt the message, we’ll repeat the key as many times as necessary to cover the whole message:
1 2 3 4 5 6 5 4 3 2 1
3 2 4 2 3 2 4 2 3 2 4
Now, we arrive at the encrypted message by adding both numbers:
1 2 3 4 5 6 5 4 3 2 1
+3 2 4 2 3 2 4 2 3 2 4
4 4 7 6 8 8 9 6 6 4 5
The resulting message (44768896645) is the encrypted message. we can decrypt message following the inverse process: Repeating the key and subtract the key:
4 4 7 6 8 8 9 6 6 4 5
-3 2 4 2 3 2 4 2 3 2 4
1 2 3 4 5 6 5 4 3 2 1
We are back at the unencrypted message.
Symmetric and Asymmetric key-based algorithm:
Symmetric Key Algorithm:
- Imagine you have a secret box and a special key.
- With symmetric key cryptography, you use the same key to lock and unlock the box. It’s like using one key for both the lock and the keyhole.
- It’s quick and easy, but you need to make sure no one else gets the key because they could unlock your box and see your secrets.
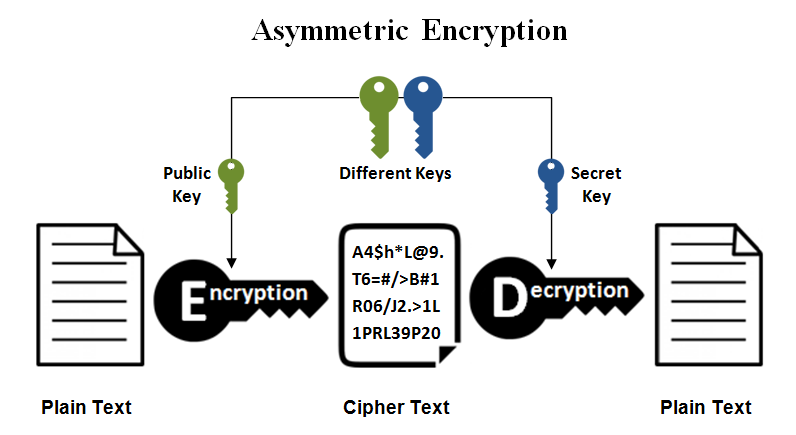
Asymmetric Key Algorithm:
- Now, picture having a magical box that creates two keys: a public key and a private key.
- With asymmetric key cryptography, you give out the public key freely, like showing everyone the lock on your box.
- But only you have the private key, like the key that opens the box. So, even though everyone can lock things in the box using the public key, only you can unlock and see what’s inside with the private key.
- It’s like having a lock that anyone can use, but only you have the key to open it.
